| Previous | Table of Contents | Next |
Assured Pipelines
If information moves from one application to another, providing separation of applications is not enough to ensure security. The method by which the information flows through the system must also be controlled. This step uses type enforcement to create a kind of “pipeline” to organize data flow between programs, called an “assured pipeline.” Type enforcement places tight control on how each program interacts with the next program in the pipeline.
This process is different from trusting the applications to interface with each other correctly. Many applications that need to be part of a system are large software components with less than reliable track records for obeying the interface definition. Using type enforcement is like having a net in the operating system that can catch the applications when they fail to follow the rules for the interface.
Type enforcement creates the pipeline by controlling access between programs. Each program has permission only to read from the stage in front of it and to write to the next stage of the pipeline. No stage of the pipeline can be bypassed. Exhibit 4 is a representation of how type enforcement controls data flow between applications through assured pipelines.
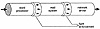
Exhibit 4. Type Enforcement Assured Pipeline
Assured pipelines provide a “divide and conquer” approach to building secure applications. Splitting a large piece of software into smaller pieces facilitates the process of analyzing and ensuring that the pieces are operating correctly. For example, consider the DoD requirement that any document printed is labeled correctly with its security label. It is not difficult to modify the printer driver to label the document, but it is difficult to prove that the printer driver labels the document accurately. The printer driver is a large program, and any modification to a large program has the potential to introduce other flaws.
On the other hand, if the labeling is done by a small program that only labels the data, the entire labeling program could be checked, and the printer driver left unmodified. Exhibit 5 shows how assured pipelines allow for the creation of smaller programs that can be analyzed for greater reliability than modifications to large software systems. In this example, type enforcement ensures that data cannot reach the printer driver unless they have gone through the labeler process.
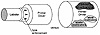
Exhibit 5. Print Driver With Type Enforcement Compared to Conventional Print Driver
Three key elements are needed to prove that the requirement of proper labeling is satisfied:
- • Type enforcement is underneath the applications controlling access to the printer driver.
- • Type enforcement ensures that the labeler process cannot be bypassed.
- • Type enforcement tables cannot be modified while the system is running.
- • Type enforcement ensures that the labeler process cannot be bypassed.
The labeler is a trusted program that ensures that only data that have been properly labeled move from the user bucket to the printer bucket.
Hosting an application on a type enforcement system requires analyzing the application to determine what resources the applications require. Often the access that an application needs can be reduced to improve security. This step may require modification to the application. The ability to separate applications, to control data flowing through the system, and to divide the application into small steps allows type enforcement to secure applications with the newest features as quickly as possible.
SIDEWINDER IMPLEMENTATION OF TYPE ENFORCEMENT
Developed by Secure Computing, Sidewinder is an Internet firewall that has incorporated the LOCK type-enforcement mechanism to provide enhanced security against Internet threats. To maximize compatibility with networks and existing protocols, Sidewinder was created by modifying BSDi UNIX. The Sidewinder is a turnkey system that resides between the Internet router and the internal network, as shown in Exhibit 6.
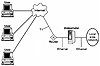
Exhibit 6. Sidewinder Internet Firewall Configuration
Traditional UNIX has been described as “a hard crunchy exterior surrounding a soft gooey center.” This description refers to the structure of UNIX systems, the core of which is an all-powerful root account. Once an attacker gets into the root account, he or she can completely compromise the system. In addition, standard UNIX does not have tight control over how data files are shared among the processes running on a system. Thus, an intruder who manages to break into one area of a system can widen the initial foothold until he or she can gain access to any file on the system. The type enforcement security mechanism closes this vulnerability.
Type enforcement in Sidewinder cannot be bypassed. Even when a process is running as root, it is constrained by type enforcement. If a hacker obtains root access, the hacker is limited to the domain in which he or she started. To compromise Sidewinder, a hacker must bypass both UNIX protection mechanisms and type enforcement, as shown in Exhibit 7. Compromising UNIX is more difficult on Sidewinder because the type-enforced honeycomb structure places vulnerable configuration files and UNIX tools out of a hacker’s reach.
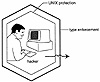
Exhibit 7. Protection Provided by Type Enforcement and UNIX
The goal of the Sidewinder system is to connect an internal network securely to the Internet. Internal users can access Internet services, such as E-mail and the World Wide Web, without exposing the internal network to unauthorized users. In addition to type enforcement, Secure Computing included three other features to make the Sidewinder firewall a more effective security system: two kernels, controlled system calls, and network separation.
Two Kernels
Sidewinder does not have the root privilege that is found on standard UNIX systems. To provide a secure method for the system administrator to modify the security-relevant information, Sidewinder uses two kernels:
The operational kernel—The normal operating state for the Sidewinder, which enforces the security policy laid out in the type enforcement tables.
The administrative kernel—This kernel is used only when the system administrator needs to perform privileged tasks, such as system configuration, on the Sidewinder. In this kernel, type enforcement checks are bypassed, which allows the administrator to modify any file, much like the root privilege on conventional UNIX systems. Because access to the administration kernel is tightly controlled by the operational kernel, only authorized users physically connected to Sidewinder can shut down the operational kernel and start the administration kernel. Exhibit 8 lists the major differences between the two kernels.

Exhibit 8. Sidewinder Kernels
| Previous | Table of Contents | Next |