The sendmail program is able to log a wide
variety of information about what it is doing. There is no default
file for recording information. Instead,
sendmail sends all such information via the Unix
syslog(3) mechanism. The disposition of messages
by syslog is determined by information in the
file /etc/syslog.conf (see Section 14.3.2). One common scheme places non-critical
messages in /var/log/syslog but routes important
messages to /dev/console or
/var/adm/messages.
The meaningful values for the logging level, and their
syslog priorities, are outlined here. Higher logging levels include the lower
logging levels. For example, logging level 2 also causes level 1
messages to be logged.
- 0
-
Minimal logging. See See this section for examples of
what is logged at this setting.
- 1
-
Serious system failures and security problems logged at LOG_CRIT or
LOG_ALERT.
- 2
-
Communication failures (e.g., lost connections or protocol failures)
logged at LOG_CRIT.
- 3
-
Malformed addresses logged at LOG_NOTICE. Transient forward/include
errors logged at LOG_ERROR. Connect timeouts logged at LOG_NOTICE.
- 4
-
Malformed qf filenames and minor errors logged at
LOG_NOTICE. Out-of-date alias databases logged at LOG_INFO.
Connection rejections (via libwrap.a or one of
the check_ rule sets) logged at LOG_NOTICE.
- 5
-
A record of each message received logged at LOG_INFO. Envelope
cloning logged at LOG_INFO.
- 6
-
SMTP VRFY attempts and messages returned to the original sender
logged at LOG_INFO. The ETRN and EXPN ESMTP commands logged at
LOG_INFO.
- 7
-
Delivery failures, excluding mail deferred because of the lack of a
resource, logged at LOG_INFO.
- 8
-
Successful deliveries logged at LOG_INFO. Alias database rebuilds
logged at LOG_NOTICE.
- 9
-
Mail deferred because of a lack of a resource logged at LOG_INFO.
- 10
-
SMTP inbound connects logged at LOG_INFO. Each key as looked up in a
database, and the result of each lookup, logged at LOG_INFO. TLS
errors logged at LOG_WARNING. AUTH= and STARTTLS errors logged at
LOG_INFO. Milter connects and replies logged at LOG_INFO.
- 11
-
All nis errors logged at LOG_INFO. The end of
processing (job deletion) logged at LOG_INFO.
- 12
-
SMTP outbound connects logged at LOG_INFO.
- 13
-
Log bad user shells, world-writable files, and other questionable
situations.
- 14
-
Connection refusals logged at LOG_INFO. More STARTTLS information
logged at LOG_INFO.
- 15
-
All incoming and outgoing SMTP commands and their arguments logged at
LOG_INFO.
- 16-98
-
Debugging information. You'll need the source to
understand this logging. You can grep(1)
LogLevel in all the .c files
to find interesting things to look for. These are logged at
LOG_DEBUG.
The forms of the LogLevel option are as follows:
O LogLevel=lev 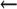 configuration file (V8.7 and later)
-OLogLevel=lev
configuration file (V8.7 and later)
-OLogLevel=lev 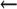 command line (V8.7 and later)
define(`confLOG_LEVEL',lev)
command line (V8.7 and later)
define(`confLOG_LEVEL',lev) 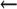 mc configuration (V8.7 and later)
OLlev
mc configuration (V8.7 and later)
OLlev 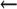 configuration file (deprecated)
-oLlev
configuration file (deprecated)
-oLlev  command line (deprecated)
command line (deprecated)
The type for lev is numeric and defaults
to 9. For the mc technique the default is also
9. Negative values are equivalent to a logging level of 0.
Logging is effective only if sendmail is
compiled with LOG defined (LOG). The
-d0.1 debugging switch (see -d0.1) can be used to see if LOG was defined for
your system.
The LogLevel option is safe. Even if it is specified from the command
line, sendmail retains its
root privilege. For security reasons the logging
level of V8.6 and later sendmail can be
increased from the command line but not decreased.
Because of their severe nature, some errors and problems are logged
even though the LogLevel option is set to zero.
Specifically:
Problems with $j and $=w that
are checked if sendmail was compiled with XDEBUG
defined:
daemon process doesn't have $j in $=w; see syslog
daemon process $j lost dot; see syslog
Failure to find your unqualified hostname or qualified domain:
My unqualified hostname (my hostname) unknown
unable to qualify my own domain name (my hostname) -- using short name
If the daemon was invoked without a full pathname:
daemon invoked without full pathname; kill -1 won't work
Normal startup of the daemon:
starting daemon (version): how
File descriptor failure if sendmail was compiled
with XDEBUG defined:
subroutine: fd number not open
Possible attacks based on a newline in a string:
POSSIBLE ATTACK from address: newline in string "string here"