| Previous | Table of Contents | Next |
Distributed systems must also address a common set of security practices, procedures, and processes because of the interaction of separate operational environments which include:
- 1. A multiplicity of components, including both physical and logical resources, that can be assigned freely to specific tasks on a dynamic basis. (Homogeneity of physical resources is not essential.) However, in general, there should be more than one resource capable of supporting any given task to maintain referential integrity of the information and the complexity of the connectivity interrelationships of heteromorphic processing environments.
- 2. A physical distribution of these physical and logical components intercommunicating through a network. Within the distributed system environment, a network is an information transmission mechanism that uses a cooperative protocol to control the transfer of information.
- 3. A high-level operating system that unifies and integrates the control of the distribution components. This high-level operating system may not exist as distinctly identifiable blocks of code. It may be merely a set of specifications or an overall, integrating philosophy incorporated into the design of the operating system for each component.
- 4. System transparency, permitting services to be requested by name only. The resource to provide the service may not need to be uniquely identified.
- 5. Cooperative autonomy, characterizing the operation as an interaction of both physical and logical resources.
- 2. A physical distribution of these physical and logical components intercommunicating through a network. Within the distributed system environment, a network is an information transmission mechanism that uses a cooperative protocol to control the transfer of information.
These five criteria form an indivisible set that defines a fully distributed system. The degree of distribution of a system depends upon the distribution of data, programs, physical hardware location, and control. This is depicted in Exhibit 1.

Exhibit 1. Distribution Continuum
To simplify this three-dimensional continuum, distributed systems may be classified into three nonoverlapping parts of the continuum, ranging from simple interactions to complex interactions of the environments. The three types of distributed systems, illustrated in Exhibit 1, are
- • Decentralized systems
- • Dispersed systems
- • Interoperable or Cooperative systems
- • Dispersed systems
Decentralized systems are characterized by a group of related but not necessarily interconnected platforms running independent copies of the same (or equivalent) applications with independent copies of data. The current state of the group is not automatically maintained. Instead of a single (central) processor with multiple users, the decentralized system has multiple (distributed) processors with single or multiple users (Exhibit 2). The processors do not necessarily communicate electronically. This characteristic prevents the system from automatically maintaining the state of the distributed system and is the primary distinction between the decentralized model and the other two distributed system models.

Exhibit 2. Decentralized Systems
Dispersed systems (Exhibit 3) are characterized by a group of related, interconnected platforms in which either the data or the software (but not both) is centralized. A dispersed system offers advantages over centralized systems in its capabilities to:
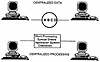
Exhibit 3. Dispersed Systems
- • Accommodate organizational change
- • More effectively deploy resources through resource sharing
- • Improve performance through intelligent matching of applications, media, access schemes, and grouping of related members
- • Lower risk of overall system failure due to hardware failures
- • More effectively deploy resources through resource sharing
The dispersed system may have centralized data with dispersed processors (as in a system with a central file server) or centralized processing with dispersed data (as with remote transaction collection and central data processing). Dispersed systems may exist on multiple platforms in a single location or on platforms in multiple locations. The hardware may be homogeneous or heterogeneous.
The processors communicate electronically, usually to request or provide data. This characteristic allows the system to automatically maintain a single, collective, real-time state of the distributed system.
Interoperable or cooperative systems (Exhibit 4) are characterized by a group of related, interconnected platforms in which both the data and the software are distributed throughout the system. The interoperable system differs from the dispersed system by eliminating the dependency of centralized data or centralized applications. The interoperable system offers the same advantages over centralized systems as the dispersed system. The difference is in the degree to which the system can cooperatively exploit these advantages.
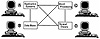
Exhibit 4. Interoperable Systems
Additionally, an interoperable system offers advantages over centralized systems in its capabilities to:
- • Combine data from dissimilar hardware platforms
- • Independently execute and test each component
Interoperable systems represent the highest level of the distributed processing continuum. In a fully interoperable system, each component is independent of all other components. Interfaces and data dependencies are implemented as messaging schemes or as data objects (consisting of data and operations). Interoperable systems may exist on multiple platforms in a single location, on platforms in multiple locations, or on multiple networks in multiple locations.
The hardware may be homogeneous or heterogeneous. The processors communicate electronically. Each component automatically maintains its own state and can provide its state on request. The existence of multiple states is the primary discriminant between the interoperable model and the other two distributed system models.
A distributed system may include characteristics of each of the three models described above. The application of security-relevant requirements from each model is necessary to build a complete security requirements set.
| Previous | Table of Contents | Next |