| Previous | Table of Contents | Next |
Law Enforcement Access
U.S. law authorizes certain government officials to intercept the wire, electronic, or oral communications of a subject under criminal investigation on obtaining a special court order. To obtain this order, the government must demonstrate that there is probable cause to believe that the subject under investigation is committing a serious felony and that communications concerning the offense will be obtained through the intercepts. Before issuing a court order, a judge must review a lengthy affidavit that sets forth all the evidence and agree with the assertions contained therein. The affidavit must also demonstrate that other investigative techniques have been tried without success, that they will not work, or that they would be too dangerous.
After the government has obtained a court order to intercept a particular line, the order is taken to the telecommunications service provider to get access to the communications associated with that line. Normally, the government leases a line from the service provider, and the service provider transmits the intercepted communications to a remote government monitoring facility over that line. If the government detects encrypted communications, the incoming line is set up to pass through a special government-controlled decrypt device as shown in Exhibit 6. The decrypt device recognizes communications encrypted with a key escrow chip, extracts the LEAF and IV, and decrypts the LEAF using the KF to pull out the UID and the encrypted session key (EKU(KS)).
The chip identifier UID is given to the escrow agents along with a request for the corresponding chip unique key components, documentation certifying that electronic surveillance has been authorized for communications encrypted or decrypted with that chip, and the serial number of the decrypt device. On receipt of the certification, the escrow agents release the corresponding encrypted key components (EK1(KU1) and EK2(KU2)) to the government. The keys are then transmitted to the government decrypt device in such a manner as to ensure that they can be used only with that device as authorized.
The device decrypts the KU1 and KU2 using the K1 and K2 respectively, computes the KU as KU1 XOR KU2, and decrypts the KS. Finally, the decrypt device decrypts the communications encrypted with KS. To accomplish all this, the device is initialized to include the KF and the K1 and K2.
When the escrow agents transmit the encrypted key components, they also transmit the expiration date for the authorized surveillance. It is anticipated that the decrypt device will be designed to destroy the KU and all information used to derive it on the expiration date. In the meanwhile, however, every time a new conversation starts with a new KS, the decrypt device can extract and decrypt the KS from the LEAF without the need to go through the escrow agents. Thus, except for the initial delay getting the keys, intercepted communications can be decrypted in real time for the duration of the surveillance. This real-time capability is extremely important for many types of cases, for example, kidnappings and planned terrorist attacks.
Because the same KS is used for communications sent in both directions, the decrypt device need not extract the LEAF and obtain the KU for both the caller and called to decrypt both ends of the conversation. Instead, it suffices to obtain the KU for the chip used with the telephone associated with the subject of the electronic surveillance.
An unauthorized person wishing to listen in on someone else’s communications would need to duplicate the capability of the government; that is, have access to the communications, a decrypt device, and the encrypted chip unique key components. Because a decrypt device cannot be built without knowledge of the classified algorithms, KF, and K1 and K2, an adversary almost certainly needs to acquire a decrypt device from the government (e.g., by theft or bribery).
PUBLIC-KEY CRYPTOSYSTEMS
In a public-key cryptosystem, or asymmetric system, each user or application has a pair of permanent or long-term keys — a public key and a private key. The public key can be freely distributed or stored in a public directory, but the private key must be known only to the user or the user’s cryptographic chip. Because the public and private keys must be mathematically related, the private key cannot be derived from the public key.
The advantage of public-key systems is that they allow the transmission of secret messages without the need to exchange a secret key. To send a message, the sender obtains the receiver’s public key and uses it to encrypt the message. The receiver than decrypts the message using its private key. The sender’s keys are not used (they would be used in a reply). Exhibit 7 illustrates this process.
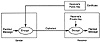
Exhibit 7. A Public-Key, or Two-Key, Cryptosystem
Public-key cryptosystems can provide secrecy but not authenticity. This is true because a third party, with access to the receiver’s public encryption key, can inject bogus ciphertext that decrypts into meaningful plaintext. To get authenticity, it is necessary to combine a public-key cryptosystem with a public-key signature system.
| Previous | Table of Contents | Next |