9.3 Administering Services by Using the Server Settings MenuServices are generally processes that wait for a request to perform an operation or provide information and then do so. The Server Settings menu provides menu items that let you administer certain services. The menu also provides the Service Configuration tool that lets you start and stop services and configure which services run at various runlevels. Red Hat Linux supports seven runlevels:
Runlevels 3 and 5 are normal system operating modes. Other modes are used transiently (levels 0, 6), for troubleshooting (levels 1, 2), or not used at all (level 4). When you associate a service with a runlevel, the service is automatically started whenever the runlevel is entered. You can set the current runlevel by issuing the command: init n where n is the number of the desired runlevel. However, it's seldom necessary to change the runlevel of a running system. You should do so judiciously, since services may be abruptly terminated during transition from one runlevel to another. To launch the Service Configuration tool, select Server
Settings Figure 9-28. The Service Configuration tool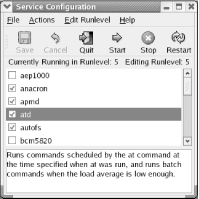 To learn about the function of a server, select the server's name. A description of the server may appear in the bottom pane of the Service Configuration window. Figure 9-28 features such a description. Not all services feature such descriptions. 9.3.1 Associating Services with RunlevelsTo associate a service with a runlevel, select the runlevel by using the Edit Runlevel menu. You can edit only for runlevels 3, 4, and 5. Despite the fact that runlevel 4 is not used, it's common to associate with level 4 any services associated with level 3. However, you need not do so. Once you've selected the desired runlevel, you can specify the services that should run when that runlevel is active. To specify that a service should run, enable the associated checkbox. To specify that a service should not run, disable the associated checkbox. Your changes to a runlevel are not automatically saved. To save them, click the Save button on the toolbar of the Service Configuration tool. 9.3.2 Starting and Stopping ServicesSuppose that the current runlevel is 3 and that a particular service is running. If you use the Service Configuration tool to specify that the service should no longer run in runlevel 3, the system does not immediately terminate the service. Similarly, the system does not immediately start a service newly specified to run in the current runlevel. Instead, the status of the service is changed the next time the specified runlevel is entered. However, you can use the Service Configuration to immediately start or stop a service. To do so, select the service and click the Start or Start button on the Service Configuration toolbar. You can also restart a service, which stops and then restarts the service. Restarting a service is useful when you've manually modified the service's configuration file, since restarting the service causes it to re-read the configuration file. 9.3.3 Hardening Your SystemMany attackers target services. Therefore, a useful step in hardening a system—that is, protecting it against attack—is disabling or removing unneeded services. To disable a service, simply ensure that the service is not associated with runlevels 3 or 5. However, it's better yet to remove the service from the system. That way, an attacker will find it more difficult to enable the service. Of course, you must not disable or remove a service that's needed on the system. So, you need to know something about a system before you tamper with it. You can discover the services for which your system is configured by examining the files in /etc/init.d. Each service is represented by a file in that directory. To learn about a service, first determine the name of the associated RPM package. To do so, issue the command: rpm -qf /etc/init.d/service
where service is the name of a service. For example, issuing the command: rpm -qf /etc/init.d/anacron tells you that the anacron service is associated with the anacron package. Often, the name of service and the name of the associated package are the same. However, this isn't always the case. Once you know the name of the associated package, you can learn about the service by issuing the command: rpm -qi package
where package is the name of the package. To disable a service, you can use the Service Configuration tool. To remove a service, you can issue the command: rpm -e package
where package is the name of the package. Occasionally, it's not possible to remove a package because another package requires it. In such a case, you can remove both packages or settle for merely disabling the unremovable package. Table 9-1 identifies several services that are seldom needed that are nevertheless installed by default in some installation configurations. Unless you have a particular need for them, you should disable or remove them from your system. Doing so is particularly important if your system is continuously connected to the Internet. However, even intermittently connected systems, such as those using dialup modems, are vulnerable to attack.
|