If you choose to program
Security Settings on the device from the Generate
Programming File page, the wizard takes you to the Security
Settings page (see figure below).
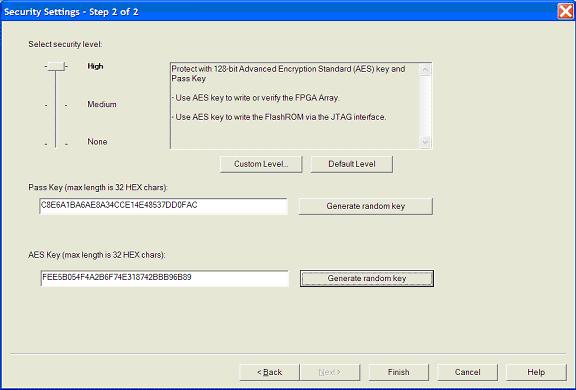
Move the sliding bar to select the security level
for FPGA and FlashROM (see table for a description of the security levels).
|
Security Level |
Security Option |
Description |
|
High
|
Protect with a 128-bit Advanced Encryption Standard (AES) key and a Pass Key |
Access to the device is protected by an AES Key and
the Pass Key.
From the JTAG interface, the Write and Verify operations of the FlashROM use a 128-bit AES encrypted bitstream. Read back of the FlashROM content via the JTAG interface is protected by the Pass Key.
Read back of the FlashROM content is allowed from the FPGA Array. |
|
Medium |
Protect with Pass Key |
The Write and Verify operations of the FPGA Array require a Pass Key.
From the JTAG interface, the Read and Write operations
on the FlashROM content require a Pass Key. You can Verify the FlashROM
content via the JTAG interface without a Pass Key. Read back of the FlashROM content is allowed from the FPGA Array. |
|
None |
No security |
The Write and Verify operations of the FPGA Array do not require keys.
The Read, Write, and Verify operations of the FlashROM content also do not require keys. |
Enter the Pass
Key and/ or the AES Key as
appropriate. You can generate a random key by clicking the Generate
random key button.
The Pass Key protects all the
Security Settings for the FPGA Array and/or FlashROM.
The AES Key decrypts FPGA Array
and/or FlashROM programming file content. Use the AES Key if you intend
to program the device at an unsecured site or if you plan to update the
design at a remote site in the future.